- Sep 9, 2025
Cyberfit to Fly: The Aircraft Information Security Ecosystem
- David Lapesa Barrera
Modern aviation depends on complex digital systems. Alongside the engines, hydraulics, and avionics, there is now a vast network of interconnected software, hardware, and communication pathways.
While operator information security protects the digital assets, IT infrastructure, and business systems of the airline or aviation service provider, aircraft information security focuses on the systems and data inside the aircraft itself. This includes everything from flight-critical software to ground-based tools that connect during maintenance. Any weakness here can affect the safety, reliability, and continuing airworthiness of the aircraft.
The upcoming adoption of EASA Part-IS requires an Information Security Management System (ISMS) for operators, but it offers limited guidance on aircraft-specific measures. On the other hand, the FAA addresses cybersecurity in aircraft systems through airworthiness guidance such as AC 119-1 “Operational Authorization of Aircraft Network Security Program” and related policy, but does not provide a comprehensive rule equivalent to Part-IS.
In this context, industry standards referenced in EASA Part-IS and FAA AC 119-1, such as EUROCAE ED-204 / RTCA DO-355 “Information Security Guidance for Continuing Airworthiness”, provide the necessary requirements and practices to address the specificities of aircraft information systems.
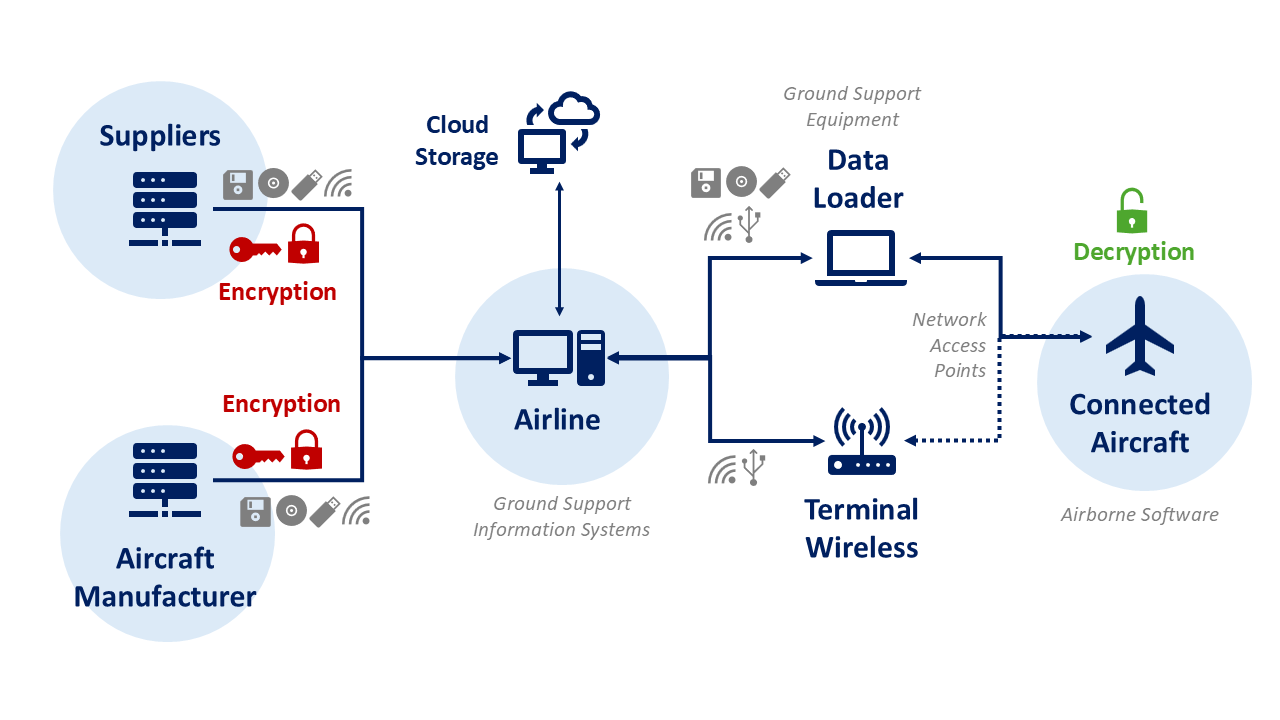
The Aircraft Information Security Ecosystem comprises multiple interrelated domains that must be managed in a coordinated manner to mitigate risks. These include the protection of airborne software, aircraft components, and the interfaces through which data flows to and from the aircraft.
Airborne Software
Airborne software refers to data or code that defines controls or is used by aircraft systems to perform specific functions. Safeguarding this software involves ensuring its authenticity, integrity, and confidentiality throughout its lifecycle, from initial development to distribution, installation, and operational use.
Historically, updates were provided via physical media such as magnetic disks, optical disks, or flash drives, transported and handled under strict physical security protocols. The adoption of Electronic Distribution of Software (EDS) enables updates to be transmitted electronically via wired or wireless connections, with authenticity and integrity verified through cryptographic signatures.
In the EDS process, the sender applies a digital signature to the software package, and the receiving system validates both the origin and the integrity of the content prior to installation. While EDS increases operational efficiency, it requires rigorous management of cryptographic keys and signature verification procedures to prevent unauthorized or altered software from being installed.
Aircraft Components
Modern digital aircraft components often store sensitive information such as encryption keys, configuration data, and operational records. These must be secured throughout their lifecycle, including transportation, storage, installation, maintenance, and decommissioning, to prevent unauthorized access or manipulation.
The global nature of the aviation supply chain, with components moving between manufacturers, operators, MROs, and storage facilities, adds further complexity and potential exposure to tampering.
Aircraft Network Access Points
Network access points are physical or wireless interfaces enabling communication between the aircraft and external systems for operational updates, maintenance data transfer, or passenger services. Examples include cockpit ports, aviaonic equipment bay connectors, cabin service panels, maintenance ports, and wireless access points.
Access points in secure zones benefit from physical protection, whereas those in accessible locations require stringent electronic access control.
Computer-Based Ground Support Equipment (GSE)
This category includes any digital device interfacing with an aircraft on the ground, such as Portable Maintenance Access Terminals (PMATs), Portable Data Loaders (PDL), Automated Test Equipment (ATE), diagnostic tools, or standard laptops equipped with approved maintenance applications.
Interfaces like USB, Ethernet, and Wi-Fi, as well as removable media, can introduce cybersecurity risks if not properly secured, since they interact with aircraft digital systems and may carry embedded threats.
Ground Support Information Systems (GSIS)
GSIS are ground-based digital systems used for the storage, management, and distribution of airborne software and related data, as well as for developing or modifying certain operator-managed software types.
These systems must be secured against threats affecting their connections to other ground-based networks and to the aircraft itself. Data transfers, whether from suppliers to operators, operator repositories to portable devices, or directly to the aircraft, must be protected to maintain integrity and prevent manipulation.
Connectivity with third-party networks, such as those of airports or MRO providers, increases the exposure surface and requires additional security measures.
Digital Certificates
Public key cryptography supports key security functions in both airborne and ground-based environments, including encryption, digital signing, and system authentication. Digital certificates bind a verified identity to a public key, enabling systems to confirm the trustworthiness of that key.
Certificates are issued by a Certificate Authority (CA), whether internal or external, that validates identity before issuing. The Public Key Infrastructure (PKI) comprises the policies, hardware, software, and procedures for the full lifecycle of certificate management.
Robust PKI governance ensures that only authenticated and authorized sources are trusted for software, communications, and data exchange.
Integrated Protection
A holistic approach across all six domains is essential. For example, a breach in GSIS can distribute altered software, a compromised maintenance device can bypass onboard safeguards, and an unprotected component can expose sensitive data. Coordinated security across stakeholders ensures the aircraft’s digital ecosystem remains resilient.
As connectivity grows, securing airborne software, networks, and ground systems is crucial to continuing airworthiness. While Part-IS provides a framework for operator security, industry standards like EUROCAE ED-204 equip professionals to implement aircraft-specific protections.
Take the lead in Aircraft Cybersecurity
Gain the skills to secure airborne systems, networks, and data across their lifecycle with our Information Security for Continuing Airworthiness course.